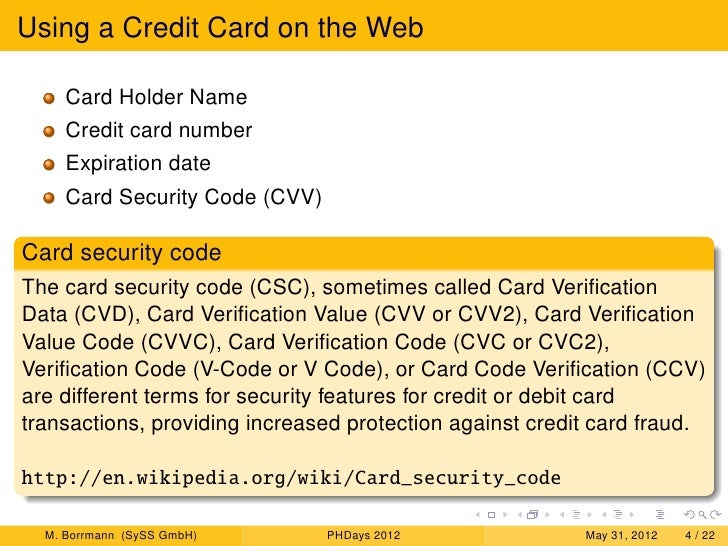
How Card Verification Value CVV/CVC iCVV CVV2/CVC2 dCVV calculation for Visa Mastercard works Documentation - How to calculate CVV - Algorythm. Ensure a 2-part 16 byte key. That is 32 hex characters. We will call this 'Key' Step 2. Ensure 16 or 19 digits PAN Card number. Ensure 4 characters of Expiration Date. Below I am sharing the latest carding dorks which you can use to get the credit card details of the people. People who are imagining what carding dorks is can read this Detailed tutorial on Google Dorks and SQL injection. Sql Injection Tool Get Cc Cvv Itunes. STEAL PREMIUM CREDIT CARD WITH SQL INJECTION We would like to thank all of our customers and partners that have helped to. Sql Injection Cvv, free sql injection cvv freeware software downloads. We list information about sql injection tool get cc cvv (Images, videos and related information.). Home Website hacking SQL Injection Tutorial With Havij. Havij is an advanced SQL injection tool which makes. Now select the Tables with sensitive information and click Get Columns button.After that select the. Exploiting SQL Injection: a Hands-on Example. In this series, we will be showing step-by-step examples of common attacks. We will start off with a basic SQL Injection attack directed at a web application and leading to privilege escalation to OS root. SQL Injection is one of the most dangerous vulnerabilities a web application can be prone to.
SQLiv is a Python-based massive SQL Injection dork scanning tool which uses Google, Bing or Yahoo for targetted scanning, multiple-domain scanning or reverse domain scanning.
SQLiv Massive SQL Injection Scanner Features
Both the SQLi scanning and domain info checking are done in a multiprocess manner so the script is super fast at scanning a lot of URLs. It’s a fairly new tool and there are plans for more features and to add support for other search engines like DuckDuckGo.
- Multiple domain scanning with SQL injection dork by Bing, Google, or Yahoo
- Targetted scanning by providing specific domain (with crawling)
- Reverse domain scanning
Using SQLiv For SQL Injection Dorks Scanning
Multiple domain scanning with SQLi dork
Simply search multiple websites from given dork and scan the results one by one: